
The most important facts in brief
Security Analytics enables companies to identify and analyze suspicious activities and security-relevant anomalies within their IT infrastructure in real time and to react appropriately. Large volumes of data from various sources – such as network traffic, user activities or log files – are intelligently correlated with each other. The aim is to identify risks at an early stage, uncover security gaps and sustainably reduce the attack surface.
With a powerful platform such as Qlik, security analytics can be integrated into existing processes and evaluated in a benefit-oriented manner. In this way, organizations not only gain transparency about their security situation, but can also quickly derive targeted measures based on sound data – a decisive advantage in the face of growing threats and complex IT landscapes.
What is security analytics – and why is it becoming increasingly important for companies?
The threat situation in the digital space is constantly growing. Companies are faced with the challenge of not only detecting security incidents, but also evaluating them in real time and responding to them in a targeted manner. This is precisely where security analytics comes in: a data-driven method for analyzing security-relevant events that relies on intelligent correlation of data sources and modern detection methods.
In contrast to traditional monitoring systems, security analytics not only enables the detection of vulnerabilities, but also the early identification of attack patterns, anomalies and suspicious activities. By connecting different systems and data sources – such as network traffic, endpoints, cloud applications or security tools – a comprehensive overview of security-relevant developments is created.
The ability to react automatically to security-relevant events is increasingly becoming a competitive factor: only those who gain knowledge about risks at an early stage can act appropriately and economically. Security analytics therefore forms the basis for modern cybersecurity strategies that rely on prevention, real-time monitoring and learning systems.
Vereinbaren Sie mit uns einen kostenfreien Beratungstermin.
Beratungstermin vereinbarenChallenges in security monitoring without integrated analytics
Many companies still rely on traditional security systems such as firewalls or manual log evaluations. These provide individual pieces of information, but without context, correlation or prioritization. The result: an unmanageable number of warnings, delayed reactions and inefficient security management processes.
A central problem is the fragmentation of data sources: Information comes from different applications, networks, cloud systems and end devices – often without a central view or standardized reporting. This not only leads to time-consuming processes, but also to missed security events that get lost in day-to-day business.
Without security analytics tools, there is also a lack of automated detection of patterns, vulnerabilities and security threats. Threats that spread across multiple systems or develop over longer periods of time often remain undetected. In addition, without integrated analysis functions, it is also difficult to prioritize security incidents – a clear disadvantage in situations where every minute counts.
Particularly in the age of complex cyber threats and hybrid IT infrastructures, intelligent tools are therefore needed that not only collect data, but also contextualize, evaluate and automatically process it – a performance promise that modern security analytics platforms fulfil.
Which data sources and methods are used in security analytics?
The success of modern security analyses depends largely on how comprehensively and intelligently relevant data is processed. It is not just the quantity that matters, but above all the quality, correlation and interpretation of the information.
Typical data sources range from network and endpoint logs, authentication events (e.g. through multi-factor authentication), cloud access, API activity, third-party threat data, internal security incidents, alarms and user behavior. This heterogeneous data provides the raw material for targeted analysis.
Specialized security analytics tools are used to derive patterns, anomalies and suspicious facts that indicate attacks, security gaps or other vulnerabilities.
| Method | Objective | Practical example |
|---|---|---|
| Anomaly detection | Detection of unusual activities | Access outside normal times through a customer account |
| Behavior analysis | Detect deviations from the usual user behavior | Sudden increase in file downloads by an employee |
| Threat data correlation | Comparison with known attack patterns | IP address appears in external threat feeds |
| Automated incident response | Triggering of predefined countermeasures | Blocking of an account in the event of a conspicuous login pattern |
The targeted use of these methods enables companies to deploy resources efficiently, assess incidents at an early stage and make concrete decisions about security measures in business operations – always based on the latest data.
Security analytics with Qlik – how to create an overview and responsiveness
Modern security analytics not only require powerful technologies, but also a solution that can be seamlessly integrated into existing IT and business structures. This is precisely where Qlik scores: the platform makes it possible to analyze security-relevant data in real time, visually process findings and make operational decisions on a reliable basis.
Qlik offers the option of flexibly connecting security-relevant data sources – whether from the cloud, from local applications or from third-party providers. The processing of large volumes of data is accelerated by in-memory technology and associative data models. This creates visual dashboards that give security managers an intuitive overview of the current security status – including drill-downs to individual events.
Particularly valuable: Qlik promotes active collaboration between IT, security teams and specialist departments. Thanks to role-based access options, even non-experts can understand and comprehend risks – a clear advantage in day-to-day business.
Qlik combines powerful data analysis with intuitive visualization and high scalability – ideal for companies of any size that want to manage security based on data.
Practical guide: How to establish security analytics in your company
The introduction of security analytics is a structured process that combines technical integration, methodical implementation and organizational integration. For security analytics to be effective in everyday life, a clear procedure is required – regardless of the tool used.
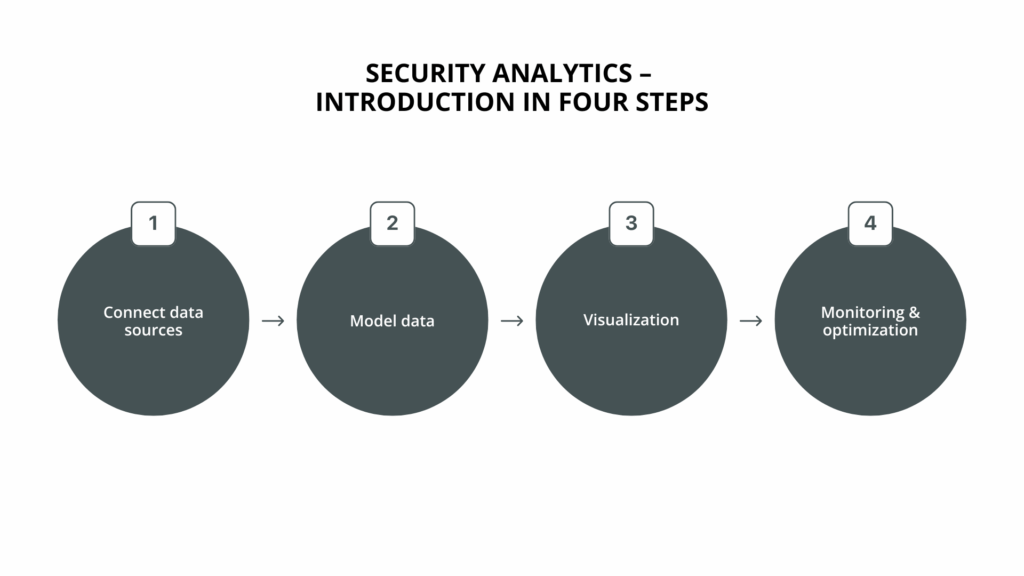
A proven approach is divided into four central task areas:
- Identify and connect data sources – such as log systems, authentication services, network monitoring, cloud platforms or security analysis tools.
- Structuring and modeling the data – to make security-relevant correlations recognizable and to be able to identify anomalies.
- Develop dashboards and visualizations – to present key findings transparently for IT, management and specialist departments.
- Ongoing monitoring and improvement – by analyzing historical incidents, recognizing recurring patterns and evaluating existing measures.
This systematic approach enables companies to professionalize their security monitoring in a targeted manner, assess risks in context and significantly improve their ability to react.
Strategically strengthening security with security analytics
A data-based approach to security is crucial in order to reduce attack surfaces, identify risks at an early stage and prioritize measures in a targeted manner. Security analytics provides the necessary transparency to evaluate security-relevant information from a wide variety of sources in a structured manner and make it usable in a targeted manner.
The combination of continuous monitoring, pattern recognition and prioritized implementation of measures significantly improves the efficiency of security processes. This not only enables companies to react more quickly to incidents, but also to deploy their resources more efficiently and strengthen the resilience of their IT infrastructure.
Security analytics also enables the systematic evaluation of key security figures in order to learn from past incidents and continuously develop your own protection. This strengthens strategic security planning and creates a reliable basis for management decision-making.
Security analytics improves the security situation, increases efficiency in dealing with incidents and increases transparency for managers and security officers.
Use security analytics in a targeted manner and measurably improve security
Security analytics provides clear added value for companies that want to improve their security situation on the basis of valid data. The aim is to identify threats, systematically analyze security events and derive well-founded measures from them.
Regardless of industry or company size, this approach allows security tasks to be managed more efficiently, vulnerabilities to be identified more quickly and security strategies to be implemented in a practical manner. The selection of suitable products and platforms should always be based on the company’s specific requirements and data sources.
Intelligently combining different methods and data sources creates comparability, transparency and measurable progress – for the benefit of IT departments, specialist departments and customers alike.
Vereinbaren Sie mit uns einen kostenfreien Beratungstermin.
Beratungstermin vereinbarenFrequently asked questions about security analytics
What is the difference between security analytics and traditional security monitoring?
The key difference lies in the analysis approach: while traditional systems often only show individual incidents, security analytics allows the correlated evaluation of many data sources in real time. This creates a holistic view that goes beyond pure alerting and enables well-founded comparisons across time, systems and locations.
For which tasks is security analytics particularly suitable?
Security analytics supports the prioritization of security incidents, the identification of anomalies, the assessment of vulnerabilities and the development of targeted measures. It is particularly helpful where large amounts of data, many systems or distributed responsibilities are involved.
What does the practical implementation of security analytics look like in everyday life?
In practice, implementation begins with the connection of relevant data sources and the definition of key areas for analysis. Dashboards, warning mechanisms and evaluations are then developed that support daily operations and are continuously adapted – based on current threat situations and experience.







