The most important facts in brief
Today, cyber security in companies is not only a technical but also a strategic core task. Attacks by cyber criminals, ransomware or targeted hacker attacks are constantly on the rise and often cause considerable financial losses and reputational damage in addition to technical failures.
Modern security concepts rely on a combination of preventative measures, continuous analysis and clear processes to identify and minimize risks at an early stage. These include effective data access management, regular security audits and company-wide awareness of threats.
Companies that firmly integrate cyber security into their corporate strategy increase their resilience, reduce their attack surface and secure their long-term ability to act in an increasingly digital and networked world.
Vereinbaren Sie mit uns einen kostenfreien Beratungstermin.
Beratungstermin vereinbarenWhy cyber security is crucial for companies today
From IT topic to corporate strategy
In many organizations, cyber security is still primarily seen as a technical issue for the IT department. But the reality is that a successful attack affects the entire company – from its operational capacity to its financial stability to its market and customer perception.
Whether a ransomware attack, data leak or targeted hacker attack – the impact often extends far beyond the immediate damage. Production downtime, contractual penalties, fines due to data breaches and long-term loss of trust among customers and partners are just some of the possible consequences.
The growing threat situation
Digitalization and the increasing networking of business processes are significantly expanding the potential attack surface of companies. Cyber criminals use automated attack tools, targeted phishing campaigns and complex malware to exploit vulnerabilities. Not only corporations, but also medium-sized companies are increasingly being targeted.
The combination of technical protective measures, clearly defined processes and a sensitized workforce is the most effective shield against cyber threats today.
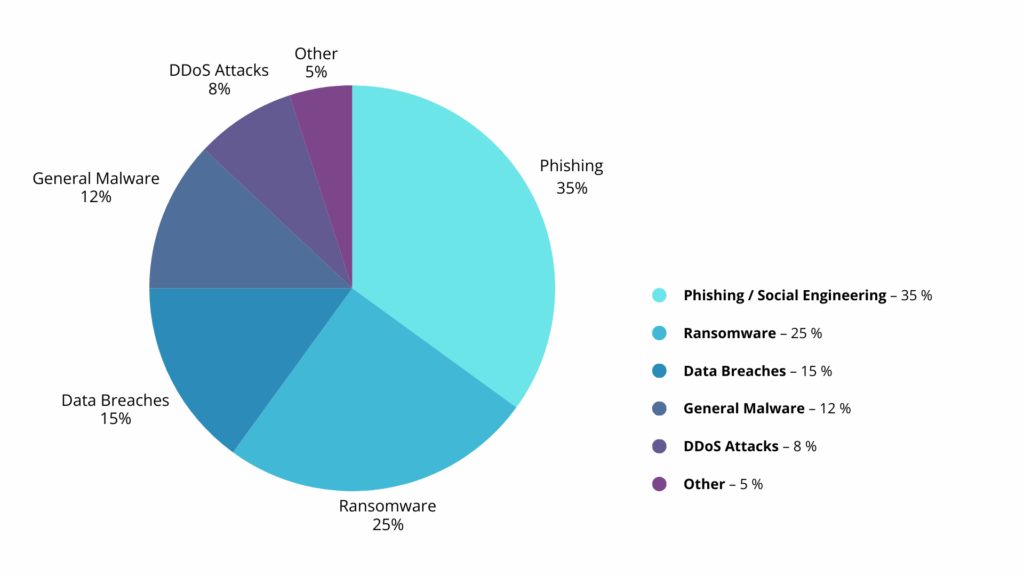
Definition and key terms of cyber security
What cyber security involves
Cybersecurity refers to all measures, technologies and processes aimed at protecting digital systems, networks, applications and data from unauthorized access, misuse, manipulation or destruction. This involves not only technical components such as firewalls or encryption, but also organizational structures, guidelines and raising employee awareness.
In the corporate context, cyber security means creating a holistic security architecture that encompasses prevention, detection, response and recovery.
Overview of relevant terms and abbreviations
- Malware: Malicious software that infects systems, steals data or sabotages processes.
- Phishing: Fraud attempts via e-mail, SMS or websites to steal access data.
- Ransomware: Malware that encrypts data and demands a ransom.
- DDoS (Distributed Denial of Service): Overloading of systems through mass requests.
- Zero-day exploit: Exploitation of a security vulnerability before a patch is available.
- APT (Advanced Persistent Threat): Long-term, targeted attack by highly specialized attackers.
Threat situation and common types of attack
Ransomware and malware
Ransomware is currently one of the biggest threats to companies. Attackers encrypt important company data and demand a ransom for its release. In addition to the immediate business interruption, this often results in high costs for recovery, forensic analysis and possible legal disputes.
Malware, on the other hand, includes all forms of malware, from Trojans to viruses and spyware. The aim is often to steal data or manipulate systems unnoticed.
Phishing and social engineering
Phishing attacks are designed to trick employees into disclosing sensitive data – for example, by using deceptively genuine emails that appear to come from an internal department or business partner. Social engineering goes even further by exploiting human weaknesses to gain access to systems or confidential information.
Zero-day exploits and advanced persistent threats (APT)
Zero-day exploits take advantage of security vulnerabilities that are not yet known to the manufacturer – often before a security update can be provided. Advanced persistent threats are highly specialized attacks that are carried out over a long period of time to steal sensitive company data or sabotage critical infrastructures.
| Attack type | Attack type Description | Example |
|---|---|---|
| Ransomware | Encrypts data and demands a ransom for decryption. | “WannaCry” attack on international companies in 2017. |
| Malware | Malicious software for data theft or system manipulation. | Trojan that reads passwords unnoticed. |
| Phishing | Deception using fake e-mails or websites to obtain data. | Fake bank e-mail for changing passwords. |
| Social engineering | Manipulation of people to disclose confidential information. | Call from an alleged IT administrator requesting access data. |
| Zero-day exploit | Exploitation of a previously unknown security vulnerability. | Attack before a security update is made available. |
| APT | Prolonged, targeted attack on strategic targets. | Infiltration of a company network over several months. |
Strategic building blocks of an effective cyber security strategy
Preventive protective measures as a foundation
Every cybersecurity company knows that a strong security concept starts with preventive measures. These include up-to-date security technologies such as firewalls, intrusion detection systems and encrypted data transmissions. Companies should also carry out regular security audits to identify and rectify vulnerabilities at an early stage. A multi-layered protection approach is particularly crucial in cloud use in order to protect data and devices from unauthorized access.
Firmly anchoring organization and processes
Technology alone is not enough to ward off cyber attacks in the long term. A clearly defined role and responsibility model ensures that all employees – from IT and management to operational departments – play their part in security. Partnerships with external security experts or providers from the cyber security industry can bring additional expertise and up-to-date security solutions into the company.
Continuous training and awareness-raising
Cyber criminals are constantly developing their methods, so continuous training is essential. Companies should launch initiatives to sensitize employees to current threats such as hacker attacks or phishing campaigns. Training and awareness programmes help to minimize human error – one of the biggest challenges.
Economic dimension of cyber security
Cybersecurity is not just a cost factor, but an investment in sales and competitiveness. Companies that invest in cyber security measures not only reduce the risk of financial losses, but also increase the trust of customers and partners. In many industries, a strong security position is now an important decision criterion for cooperation.

Data-driven cyber security
From reactive protection to proactive analysis
For a long time, cyber security and IT security were highly reactive: an attack happened – and then damage limitation began. Today, data analysis enables a proactive approach in which suspicious activities are detected before a successful attack occurs. This allows cyber attacks to be blocked at an early stage and security measures to be strengthened in a targeted manner.
Threat detection in real time
Modern threat detection platforms collect and analyze data from various areas of the IT infrastructure in fractions of a second – from end devices to networks and cloud environments. Intelligent systems filter out anomalies that indicate the activities of cyber criminals or hackers.
Decision-making basis for security strategies
Data-driven cyber security also means that security measures are evaluated using clearly defined KPIs. In this way, companies not only see the current status of their defences, but can also identify opportunities for optimization – for example by adapting guidelines, making targeted investments in new technologies or training employees.
| KPI | Significance | Benefit |
|---|---|---|
| Mean Time to Detect (MTTD) | Average time until a threat is detected | Shorter times reduce potential damage |
| Mean Time to Respond (MTTR) | Average time to respond to an attack | Faster responses minimize downtime |
| Blocked Intrusion Attempts | Number of blocked intrusion attempts | Shows effectiveness of prevention measures |
| Patch compliance rate | Percentage of currently patched systems | Reduces attack surface and risk due to known vulnerabilities |
| User Awareness Score | Evaluation of employee sensitization | Strengthens defenses against social engineering and phishing |
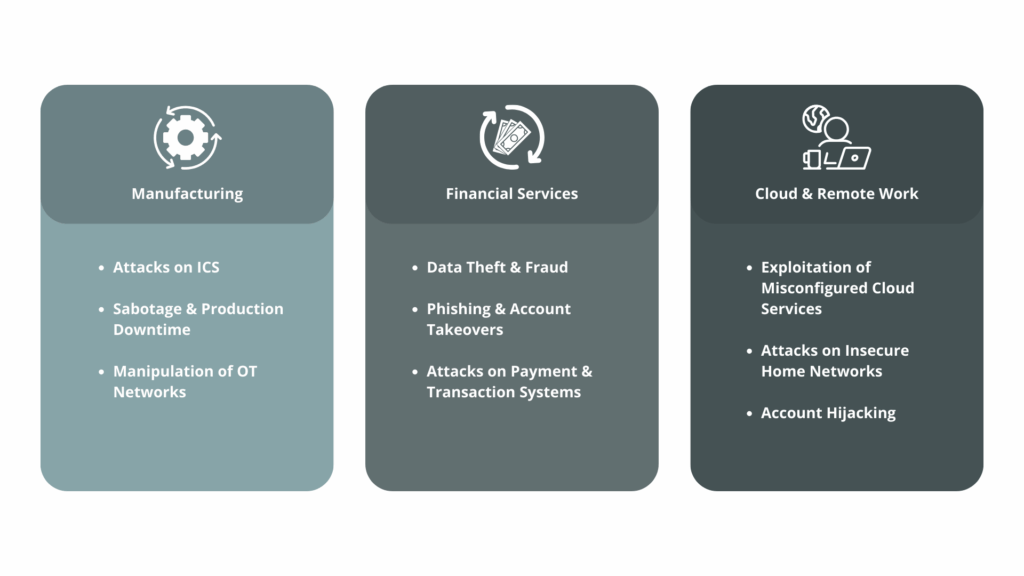
Practical examples and industry peculiarities
Production & Industry 4.0
In networked manufacturing, the risk of cyber criminals disrupting or sabotaging production systems is increasing. Attacks on industrial control systems (ICS) can lead to considerable downtime and financial losses. Effective protection here requires security measures that cover both traditional IT systems and OT (operational technology) infrastructures. Tip: Regular network segmentation and checking remote access minimize the attack surface.
Financial Services & Compliance
Banks and insurance companies are among the preferred targets of cybercrime, as highly sensitive data and financial assets are processed here. The sector is subject to strict regulatory requirements, such as the GDPR or special financial market guidelines. The structured use of monitoring systems, clear access controls and compliance dashboards is a top priority here, not only to prevent attacks but also to be able to prove compliance with all regulations.
Cloud environments and remote work
With the shift of many business processes to the cloud and the increase in remote working, new attack vectors are emerging. Criminals are specifically exploiting incorrectly configured cloud services or insecure home networks. In addition to technical protection measures such as multi-factor authentication, companies should therefore also provide organizational tips and guidelines for secure remote working. Publications on best practices can help to raise security awareness among the workforce.
Challenges and solutions
Technological hurdles
Many companies struggle with a historically grown IT landscape in which different systems coexist and do not communicate optimally with each other. This fragmentation makes it difficult to consistently monitor and respond to security incidents. In addition, there is often a lack of specialized security experts to detect and defend against complex attacks in a timely manner.
Organizational barriers
In some companies, cyber security is still seen as an isolated task for the IT department. If there is a lack of company-wide integration, gaps arise in processes, coordination and responsibilities. A holistic approach that involves management, specialist departments and IT in equal measure is crucial.
Legal and regulatory requirements
Companies not only have to meet technical standards, but also comply with legal requirements such as the GDPR or industry-specific security guidelines. The large number of publications and standards often makes it difficult to maintain an overview. Regular reviews and a clearly documented security concept are therefore mandatory.
- Outdated systems: Plan for regular updates and modernization of the IT infrastructure.
- Shortage of specialists: Promote internal training and involve external experts.
- Missing processes: Define clear roles, responsibilities and escalation paths.
- Regulatory complexity: using compliance management systems and conducting audits.
- Insufficient sensitization: Establish regular training and awareness campaigns.
Outlook: Cybersecurity of the future
AI-supported defense systems
In the coming years, cyber criminals will continue to refine their methods – from automated attacks to targeted, multi-stage campaigns. Companies are increasingly responding to this with AI-supported defense systems that can analyze suspicious activities in real time and automatically initiate countermeasures. These systems continuously learn from past attacks and adapt their detection models to new threats.
Automated incident response
The speed with which a security incident is detected and resolved is crucial. In the future, platforms that enable automated incident response will play a central role – from isolating affected systems to blocking malicious IP addresses and generating forensic reports. Providers in a range of technology fields – from endpoint security to cloud monitoring – are driving this development.
Resilient security architectures
In the long term, the focus will be more on resilient security architectures that not only prevent attacks, but also minimize their impact. This includes zero-trust models, micro-segmented networks and adaptive access controls. Companies that implement such concepts early on will secure a decisive competitive advantage over cyber criminals.
Safety culture as a competitive advantage
Today, cyber security is a strategic core competence of every company. The threat from cyber criminals is constantly growing – both in terms of frequency and complexity. Those who only act reactively risk their ability to act, reputation and financial stability.
Effective protection is based on a combination of technical measures, clear processes, continuous employee training and data-based analyses. This allows risks to be identified at an early stage and reduced in a targeted manner.
It is crucial to understand cyber security as an ongoing process that is regularly adapted to new threats. Companies that embed this culture strengthen their resilience and secure a clear competitive advantage.